Your How hackers launder money images are ready. How hackers launder money are a topic that is being searched for and liked by netizens now. You can Download the How hackers launder money files here. Get all royalty-free images.
If you’re searching for how hackers launder money images information connected with to the how hackers launder money interest, you have come to the right blog. Our site always provides you with suggestions for viewing the highest quality video and image content, please kindly surf and find more enlightening video content and images that match your interests.
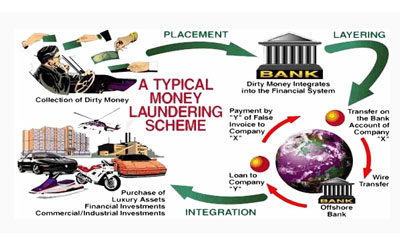
How Hackers Launder Money. The methods by which money may be laundered are varied and can range in sophistication. Many regulatory and governmental authorities quote estimates each year for the amount of money laundered either worldwide or within their national economy. The hackers would need a minimum of 21 further hacked bank accounts whose ATM cards they posses to withdraw the money out. However hackers created multiple intermediate wallets and distributed the funds to make them untraceable.
 Binance Fails To Prevent Hackers From Laundering Stolen Cryptocurrency Funds Wallstreet Cryptocurrency Vulnerability Cyber Security From pinterest.com
Binance Fails To Prevent Hackers From Laundering Stolen Cryptocurrency Funds Wallstreet Cryptocurrency Vulnerability Cyber Security From pinterest.com
Covert data collection finds that PayPal and other digital payment systems are also employed by cyber criminals to launder money. They may withdraw money from ATMs. When the theft is from a bank account the criminal will try to weave a complex web of transfers through various countries and payment systems to complicate efforts to freeze the funds. All these things are small problems in the grand scheme of things. According to a recent report from CoinDesk analytical firm Coinfirm have been tracking the 7000 SegWitCoin BTC worth of crypto originally stolen from Binance on May 7. Although it should be said that some ways of laundering money are specific to the industry where the loot originates From.
The methods by which money may be laundered are varied and can range in sophistication.
Another method used is what the cyber security firm Armor refers to in its 2019 Black Market Report as a kind of turn-key money laundering service. The other option is of purchase discounting. The hackers would need a minimum of 21 further hacked bank accounts whose ATM cards they posses to withdraw the money out. While you might be aware of some of the more common money laundering techniques here is a detailed description of the methods of money laundering. The methods by which money may be laundered are varied and can range in sophistication. In 2019 hackers stole 283 million worth of cryptocurrencies in 11 hacks.
 Source: pinterest.com
Source: pinterest.com
Money laundering is a critical step in the cyber crime process which is experiencing some changes as hackers and their criminal colleagues continually alter and optimize payment mechanisms. However hackers created multiple intermediate wallets and distributed the funds to make them untraceable. They may order goods to their own or another address. In 2019 hackers stole 283 million worth of cryptocurrencies in 11 hacks. Covert data collection finds that PayPal and other digital payment systems are also employed by cyber criminals to launder money.
 Source: id.pinterest.com
Source: id.pinterest.com
All these things are small problems in the grand scheme of things. They had proceeded to launder 23 million in Bitcoin by charging their payments onto pre-paid debit cards then withdrawing the money from ATMs across Manhattan and New Jersey for more than 1 million. Why the hackers used exchanges to launder their money Rich Sanders the blockchain forensics analyst said that sometimes hackers push funds through large exchanges to implement a tactic known as chain-hopping whereby hackers use exchanges to buy small amounts of various cryptocurrencies and send them to different exchanges using different accounts. The money-laundering process is especially interesting and unusual in the crypto world compared to the traditional world of finance. They may move funds to other accounts to throw potential trackers off the scent.
 Source: pinterest.com
Source: pinterest.com
The other option is of purchase discounting. All these things are small problems in the grand scheme of things. Another method used is what the cyber security firm Armor refers to in its 2019 Black Market Report as a kind of turn-key money laundering service. Of the total 199 25 accounts collected 46 of the funds. In this article we will investigate Upbits stolen money by following the transactions created by hackers in subsequent days and months.
 Source: pinterest.com
Source: pinterest.com
How easy is it to launder money on Binance. Smurfing A commonly used money laundering method smurfing involves the use of multiple individuals andor multiple transactions for making cash deposits buying monetary instruments or bank drafts in amounts under the reporting threshold normally around 10000. It should also be said that hacking doesnt only involve electronic money for example one can hack a cash point and walk away with hard currency. Although it should be said that some ways of laundering money are specific to the industry where the loot originates From. The hackers would need a minimum of 21 further hacked bank accounts whose ATM cards they posses to withdraw the money out.
 Source: pinterest.com
Source: pinterest.com
Among these hacks hackers also successfully targeted the Upbit exchange. Although it should be said that some ways of laundering money are specific to the industry where the loot originates From. They may order goods to their own or another address. It should also be said that hacking doesnt only involve electronic money for example one can hack a cash point and walk away with hard currency. However hackers created multiple intermediate wallets and distributed the funds to make them untraceable.
 Source: pinterest.com
Source: pinterest.com
They may order goods to their own or another address. All these things are small problems in the grand scheme of things. They may withdraw money from ATMs. Almost all money that is hacked is one way or the other converted to cash. While you might be aware of some of the more common money laundering techniques here is a detailed description of the methods of money laundering.
 Source: pinterest.com
Source: pinterest.com
Upbit hackers initial wallet 6 intermediate wallets Bitys wallet 7th hop. How easy is it to launder money on Binance. They may order goods to their own or another address. Although it should be said that some ways of laundering money are specific to the industry where the loot originates From. Of the total 199 25 accounts collected 46 of the funds.
 Source: pinterest.com
Source: pinterest.com
In this article we will investigate Upbits stolen money by following the transactions created by hackers in subsequent days and months. The other option is of purchase discounting. Among these hacks hackers also successfully targeted the Upbit exchange. Once the cybercriminals have transferred stolen money to an account using malware social engineering or an insider the mules come into play. They may move funds to other accounts to throw potential trackers off the scent.
 Source: pinterest.com
Source: pinterest.com
Covert data collection finds that PayPal and other digital payment systems are also employed by cyber criminals to launder money. They may order goods to their own or another address. How easy is it to launder money on Binance. The other option is of purchase discounting. The hackers would need a minimum of 21 further hacked bank accounts whose ATM cards they posses to withdraw the money out.
 Source: pinterest.com
Source: pinterest.com
Almost all money that is hacked is one way or the other converted to cash. A closer inspection of this ecosystem suggests that just 199 deposit addresses received 80 of all funds sent by ransomware groups in 2020. In this article we will investigate the Upbit hack and follow the stolen cryptocurrencies using Coinpath APIsWhat is CoinpathCoinpath APIs provide blockchain money flow analysis for more than 24 blockchains. Upbit hackers initial wallet 6 intermediate wallets Bitys wallet 7th hop. Pretty easy as it turns out as the same hackers who stole from the exchange have now used it to sell off some of their ill-gotten digital currency.
 Source: pinterest.com
Source: pinterest.com
While you might be aware of some of the more common money laundering techniques here is a detailed description of the methods of money laundering. Pretty easy as it turns out as the same hackers who stole from the exchange have now used it to sell off some of their ill-gotten digital currency. The other option is of purchase discounting. Among these hacks hackers also successfully targeted the Upbit exchange. They may withdraw money from ATMs.
 Source: in.pinterest.com
Source: in.pinterest.com
Another method used is what the cyber security firm Armor refers to in its 2019 Black Market Report as a kind of turn-key money laundering service. Once the cybercriminals have transferred stolen money to an account using malware social engineering or an insider the mules come into play. Why the hackers used exchanges to launder their money Rich Sanders the blockchain forensics analyst said that sometimes hackers push funds through large exchanges to implement a tactic known as chain-hopping whereby hackers use exchanges to buy small amounts of various cryptocurrencies and send them to different exchanges using different accounts. Upbit hackers initial wallet 6 intermediate wallets Bitys wallet 7th hop. They may withdraw money from ATMs.
 Source: pinterest.com
Source: pinterest.com
The methods by which money may be laundered are varied and can range in sophistication. Smurfing A commonly used money laundering method smurfing involves the use of multiple individuals andor multiple transactions for making cash deposits buying monetary instruments or bank drafts in amounts under the reporting threshold normally around 10000. Among these hacks hackers also successfully targeted the Upbit exchange. Money laundering is a critical step in the cyber crime process which is experiencing some changes as hackers and their criminal colleagues continually alter and optimize payment mechanisms. Upbit hackers initial wallet 6 intermediate wallets Bitys wallet 7th hop.
This site is an open community for users to do submittion their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site helpful, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how hackers launder money by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.