Your How terrorists might usually secure financing images are available in this site. How terrorists might usually secure financing are a topic that is being searched for and liked by netizens today. You can Download the How terrorists might usually secure financing files here. Find and Download all royalty-free vectors.
If you’re looking for how terrorists might usually secure financing images information connected with to the how terrorists might usually secure financing keyword, you have pay a visit to the right blog. Our website frequently gives you hints for refferencing the maximum quality video and image content, please kindly hunt and locate more informative video articles and graphics that fit your interests.
How Terrorists Might Usually Secure Financing. The Obama Administration must make reducing that risk a top priority of US. 2001 session of the Working Group of the Sixth Committee. Terrorists need money and other assets for weapons but also training travel and accommodation to plan and execute their attacks and develop as an organisation. Legislative efforts to help law enforcement agencies wrestle with the phenomenon of going dark will never lead to a return to the status quo ante however.
 Analysis Of Terrorist Attack Scenarios And Measures For Countering Terrorist Threats Intechopen From intechopen.com
Analysis Of Terrorist Attack Scenarios And Measures For Countering Terrorist Threats Intechopen From intechopen.com
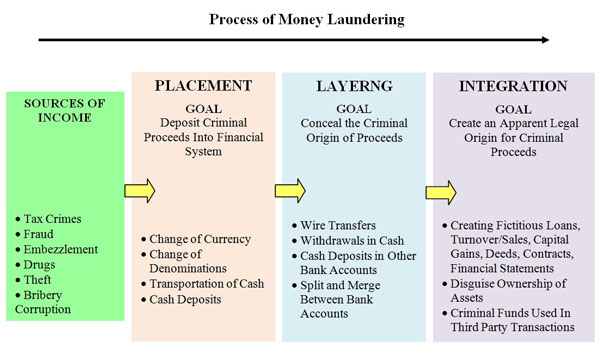
Our National Strategy for Combating Terrorism first published in February 2003 recognizes that we are at war and that protecting and defending the Homeland. Click card to see definition. In examining terrorist related financial activity FATF experts have concluded that terrorists and their support organisations generally use the same methods as criminal groups to launder funds. Since September 11 2001 the United States has faced a real and serious threat from terrorist action. It implies measures to address the conditions conducive to the spread of terrorism including the lack of rule of law and. Terrorism is in the broadest sense the use of intentional violence to achieve political aims.
Since September 11 2001 the United States has faced a real and serious threat from terrorist action.
Acquiring securing and disbursing. TERRORISTS HAVE DEVELOPED NEW WAYS OF FINANCING THEIR OPERATIONS Since terrorists are outlaws unable to hold territory and openly collect taxes their finances are necessarily clandestine and often depend on criminal activity. Overview of Americas National Strategy for Combating Terrorism. Which one of the following is NOT an early indicator of a potential insider threat. The first step in a risk management program is a threat assessment. The ISC standard only addresses man-made threats but individual agencies are free to expand upon the threats they consider.
 Source: pinterest.com
Source: pinterest.com
The ISC standard only addresses man-made threats but individual agencies are free to expand upon the threats they consider. Surveillance can be performed through either stationary or mobile means. Funding Suspicious transactions involving large cash payments deposits or withdrawals are common signs of terrorist funding. Antiterrorism Scenario Training Page 3 True. Consequently methods vary from place to place and over time.
Source:
Although the primary political objectives of terrorist groups vary depending on the group eg the political objectives of Al Qaeda differ from those of Aum Shinrikyo terrorist actions throughout history have nevertheless shared certain common characteristics and objectives. Click card to see definition. 1 December 2010 Press Conference UN Website 4 White J. Consequently methods vary from place to place and over time. As noted terrorism financing expert Dr.
 Source: pinterest.com
Source: pinterest.com
Acquiring securing and disbursing. Cash and cash-like entities tangible goods and intangibles. Disrupting and preventing these terrorism-related financial flows and transactions is one of the most effective ways to fight terrorism. References 1 Richardson L. 2001 session of the Working Group of the Sixth Committee.
 Source: pinterest.com
Source: pinterest.com
Terrorists increasingly turn to the Internet as a means of communication with one another and with the rest of the world. 1 December 2010 Press Conference UN Website 4 White J. This article describes how terrorists have cultivated the web to suit. Which of the following propositions most accurately describes the status of captured terrorists. Although funding from legitimate sources need not be laundered there is nevertheless often a need for terrorists to obscure or disguise links between it and its legitimate funding sources.
 Source: researchgate.net
Source: researchgate.net
Actual terrorists may contemplate many modes of attack but keep returning to common forms such as vehicle attacks. Congress in 2010 a key vulnerability of large terrorist groups such as Hamas and Hezbollah is their need for a large flow of external funds necessitated by the local populations inability to finance all of the infrastructure needed to provide essential services Identifying and exploiting terrorists. State-sponsored terrorism is government support of violent non-state actors engaged in terrorism. States can sponsor terrorist groups in several ways including but not limited to funding terrorist organizations providing training supplying weapons and hosting groups within their borders. It is used in this regard primarily to refer to violence during peacetime or in the context of war against non-combatants mostly civilians and neutral military personnel.
 Source: intechopen.com
Source: intechopen.com
A threat assessment considers the full spectrum of threats ie natural criminal terrorist accidental etc for a given facilitylocation. Cash and cash-like entities tangible goods and intangibles. Victor Dostov and Pavel Shust 2014 suggest that additional financial support for terrorists may come. The first step in a risk management program is a threat assessment. Hamed Tofangsaz 2015 believes that terrorists require three types of financing.
 Source: pinterest.com
Source: pinterest.com
Victor Dostov and Pavel Shust 2014 suggest that additional financial support for terrorists may come. Click card to see definition. Victor Dostov and Pavel Shust 2014 suggest that additional financial support for terrorists may come. Congress in 2010 a key vulnerability of large terrorist groups such as Hamas and Hezbollah is their need for a large flow of external funds necessitated by the local populations inability to finance all of the infrastructure needed to provide essential services Identifying and exploiting terrorists. Actual terrorists may contemplate many modes of attack but keep returning to common forms such as vehicle attacks.
 Source: pinterest.com
Source: pinterest.com
As noted terrorism financing expert Dr. References 1 Richardson L. TERRORISTS HAVE DEVELOPED NEW WAYS OF FINANCING THEIR OPERATIONS Since terrorists are outlaws unable to hold territory and openly collect taxes their finances are necessarily clandestine and often depend on criminal activity. The report commissioned by NTI finds that the world still faces a very real risk that terrorists could get a nuclear bomb. America is at war with a transnational terrorist movement fueled by a radical ideology of hatred oppression and murder.
 Source: pinterest.com
Source: pinterest.com
References 1 Richardson L. The ISC standard only addresses man-made threats but individual agencies are free to expand upon the threats they consider. Which of the following propositions most accurately describes the status of captured terrorists. Antiterrorism Scenario Training Page 3 True. Terrorists increasingly turn to the Internet as a means of communication with one another and with the rest of the world.
 Source: pinterest.com
Source: pinterest.com
It is used in this regard primarily to refer to violence during peacetime or in the context of war against non-combatants mostly civilians and neutral military personnel. Collections for donations the solicitation for money and criminal activity are also warning signs. Matthew Levitt observed when he testified before the US. The ISC standard only addresses man-made threats but individual agencies are free to expand upon the threats they consider. 3 Head of UN Counter-Terrorism Committee Executive Directorate.
Source:
Although the primary political objectives of terrorist groups vary depending on the group eg the political objectives of Al Qaeda differ from those of Aum Shinrikyo terrorist actions throughout history have nevertheless shared certain common characteristics and objectives. Surveillance can be performed through either stationary or mobile means. Consequently methods vary from place to place and over time. Disrupting and preventing these terrorism-related financial flows and transactions is one of the most effective ways to fight terrorism. Counter-terrorism strategies that seek to prevent acts of terrorism prosecute those responsible for such criminal acts and promote and protect human rights and the rule of law.
 Source: it.pinterest.com
Source: it.pinterest.com
Antiterrorism Scenario Training Page 3 False. 1 December 2010 Press Conference UN Website 4 White J. The first step in a risk management program is a threat assessment. The rights of captured terrorists are affected by what their designation is when captured. 2006 What terrorists want John Murray 2 UN Ad Hoc Committee on Terrorism 2001 Informal texts of article 2 of the draft comprehensive convention Document AC656L9.
Source:
It implies measures to address the conditions conducive to the spread of terrorism including the lack of rule of law and. America is at war with a transnational terrorist movement fueled by a radical ideology of hatred oppression and murder. The importance of combating terrorist financing. The report commissioned by NTI finds that the world still faces a very real risk that terrorists could get a nuclear bomb. Although the primary political objectives of terrorist groups vary depending on the group eg the political objectives of Al Qaeda differ from those of Aum Shinrikyo terrorist actions throughout history have nevertheless shared certain common characteristics and objectives.
This site is an open community for users to share their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site beneficial, please support us by sharing this posts to your preference social media accounts like Facebook, Instagram and so on or you can also save this blog page with the title how terrorists might usually secure financing by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.